By Anthony Candeias, CISO, Professor, Advisor
As artificial intelligence rapidly transitions from experimentation to production, organizations are prioritizing speed to market over structured oversight. Businesses, driven by the promise of competitive gains, often implement AI systems with limited foresight into governance, risk, and compliance (GRC) implications. Meanwhile, regulatory bodies are working to define how AI should be measured, monitored, and governed at scale. In this vacuum, guardrails are sparse, and frameworks for ethical deployment, bias mitigation, and data integrity remain underdeveloped if you do not have a strong AI Security solution implemented.
This misalignment places CISOs and technology leaders in a precarious position. Without clear regulatory benchmarks at the outset, AI deployments frequently proceed without the controls necessary to ensure long-term compliance. When legislation materializes often with prescriptive requirements for transparency, accountability, and explainability security teams are forced to retroactively adapt. The result is a growing operational burden: retrofitting AI systems after deployment, managing technical debt, and realigning architectures to conform to standards that did not exist when implementation began.
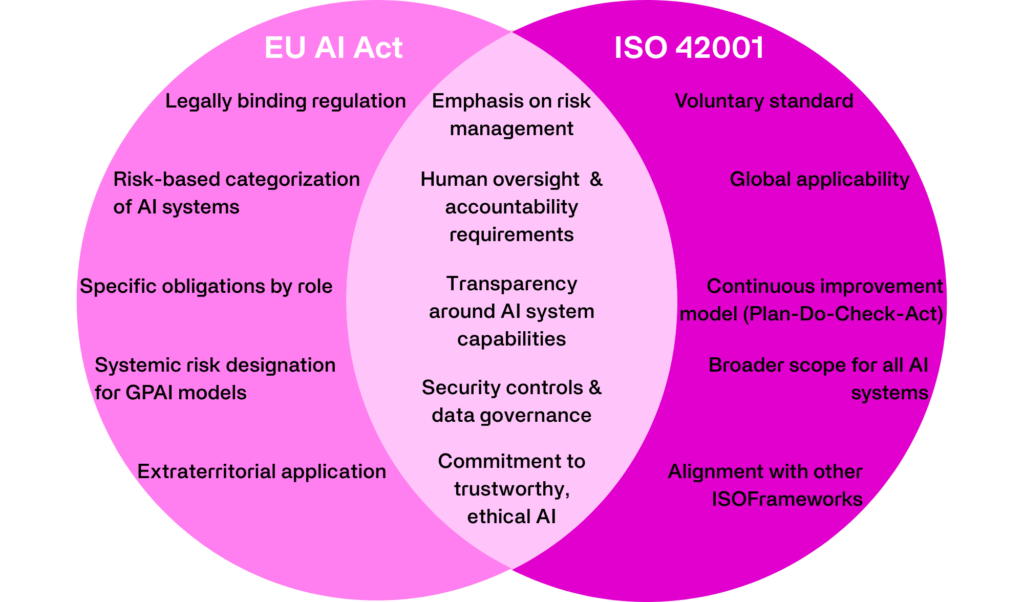
Two of the most important frameworks shaping the path forward are the EU AI Act and ISO 42001. Security and governance teams need to understand how these frameworks fit together, and more importantly, where they don’t.
To help clarify this, I’ve broken down the overlap and divergence into a simple Venn diagram model, followed by actionable guidance for AI governance committees and CISOs.
Comparing the EU AI Act & ISO 42001
What This Means for Security Teams
Most CISOs I speak with on AI regulation guidance are looking for operational clarity. Here’s how I break it down:
- If you’re operating in or selling into the EU: Start with the EU AI Act. It’s not optional, and the risk of enforcement (and fines) is very real. The key is to understand your role in the AI value chain (provider, deployer, etc.) and classify your AI systems by risk level. From there, map out the requirements accordingly—especially for high-risk systems and GPAI models.
- If you’re looking to establish a baseline AI governance model: That’s where ISO 42001 shines. It gives you a structured, repeatable approach to building your AI management system. It won’t replace compliance obligations under the AI Act, but it can operationalize your governance processes and reduce future rework. Bonus: it integrates nicely with ISO 27001 if you're already down that path.
Where Teams Go Wrong
Many teams treat these as interchangeable. They’re not. One is regulation, the other is a standard. The EU AI Act will tell you what you must do. ISO 42001 helps you define how you get it done.
Another common mistake: focusing exclusively on high-risk systems. Even “minimal-risk” use cases, like productivity bots or customer-facing LLMs, can cause brand damage, privacy violations, or bias-related fallout if not handled responsibly. ISO 42001 helps you cover those blind spots.
Final Thought: Think Layered, Not Redundant
You don’t need two separate programs—what you need is alignment. Use the EU AI Act as your regulatory floor and ISO 42001 as your operational scaffolding. Together, they provide both the why and the how of responsible AI.
And for security teams like mine, that’s not just about ticking boxes, it’s about ensuring that the systems we deploy today don’t become the risks we inherit tomorrow.